A pair of hackers has devised a way to bypass Apple's "Activation Lock" feature, a remote "kill switch" that lets iOS users lock down stolen or lost iPhones. But who will use it more: people who accidentally locked themselves out of their devices, or plain thieves?
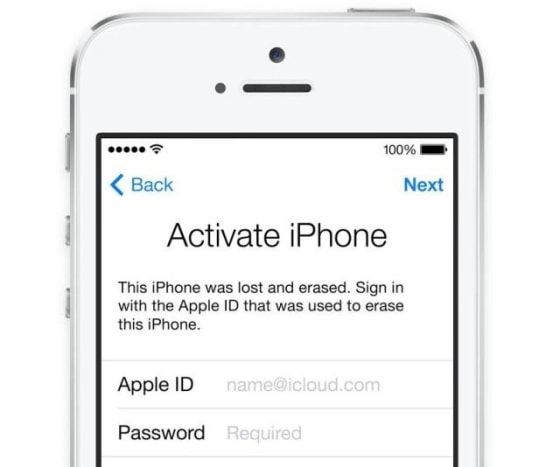
The iOS feature remotely wipes data from the device and locks it. If someone tries to use the phone, it asks for the original owner's iCloud ID — and won't start without it.
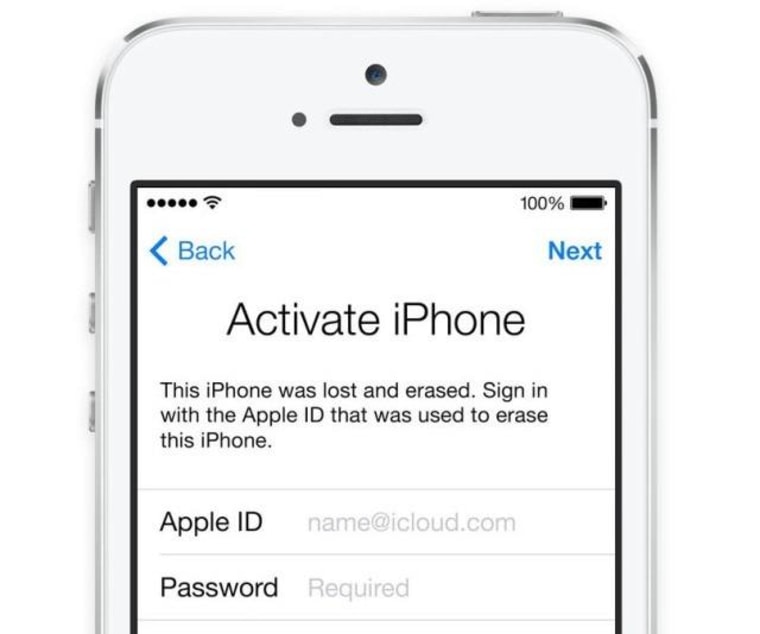
Team doulCi's ("iCloud" spelled backwards, roughly) hack is simple to implement: Users must add a single IP address to their "hosts" file, which lists trusted addresses on the Internet, and then launch iTunes and plug in the phone. Dutch news site De Telegraaf reports that the team contacted Apple about the vulnerability, but decided to go public when there was no response.
It's likely that the hack uses a "man-in-the-middle" type attack to modify or imitate the normal communications made between the app and Apple's iCloud verification servers. Whatever the method, it seems to work: Twitter is swarming with people thanking the hackers for helping unlock their phone.
The occasional appearance of a picture showing five or six recently activated phones, however, suggests some might be using the service for nefarious, or at least grey-market, purposes. A phone "found" at a crowded bar and locked using Apple's service would be worthless — unless someone came up with a way to bypass it.
And the hack itself, since it relies on users voluntarily submitting to unknown traffic to and from the hackers' IP, could very easily be used for evil as well. If it can interfere with official Apple software traffic, why not your browser, or on the phone itself?
Still, any tool is susceptible to being misused, and Team doulCi's method could help people locked out of their own device to save a couple hundred bucks. But they do so at their own risk.
More information on the method used will be made available later, the hackers said on their website.